AI-Powered Attacks via Model Context Protocol (MCP)
From Context to Compromise
Table of Contents
1. Introduction
2. What is MCP?
3. Why MCP matters for Pentesters and Security Professionals
4. Configuring MCP Server, Burp Suite, and Claude AI
5. Steps to set up the MCP Server in Notion
6. Putting it all to work
7. Security concerns with MCP
8. How to achieve a local setup?
9. Conclusions
INTRODUCTION
Picture this: It’s 2 in the morning. You’ve been testing a web app for hours. You’re capturing requests, going through endpoints, and checking every parameter manually. Your eyes hurt from staring at headers and logs for too long, but you still have a few more apps to test before the client deadline.
If you’ve ever done serious pentesting or bug hunting, this probably feels familiar.
That being said, everyone knows that manual testing takes a lot of time and energy. Repeating the same tasks, finding patterns, checking for common bugs, and matching data from multiple tools can burn us out quickly. Even if you’re good at it, it limits how deep or fast you can go.
But what if I told you that things are changing now? 🤔 I am not talking about replacing humans. I am talking about using AI as an extra hand—something that helps you find issues faster and focus on the things that matter.
That’s where Model Context Protocol (MCP) comes in. It’s a new way to connect AI tools with security tools, so you can actually make AI work with your real-world pentesting setup.
MODEL CONTEXT PROTOCOL, or MCP, as you might or might not have heard about it. UNTIL NOW. As we all know, the world of AI is revolutionizing daily, and all we can think of is using AI assistants to help with our day-to-day activities. RIGHT? In November 2024, everything changed when Anthropic introduced a new protocol that took the use of AI assistants 100 steps further. It’s called Model Context Protocol.
WHAT is MCP?
MCP is like a universal translator that helps LLM Models communicate with different software and services using a common language. It is literally an “Infinity Stone That Grants AI Tools Superpowers.”
A more textual and technical definition of MCP would be:
Model Context Protocol is an open, light-weight protocol that works as a standard bridge between LLMs and other external services, tools, APIs, or files without needing a custom integration for each one.
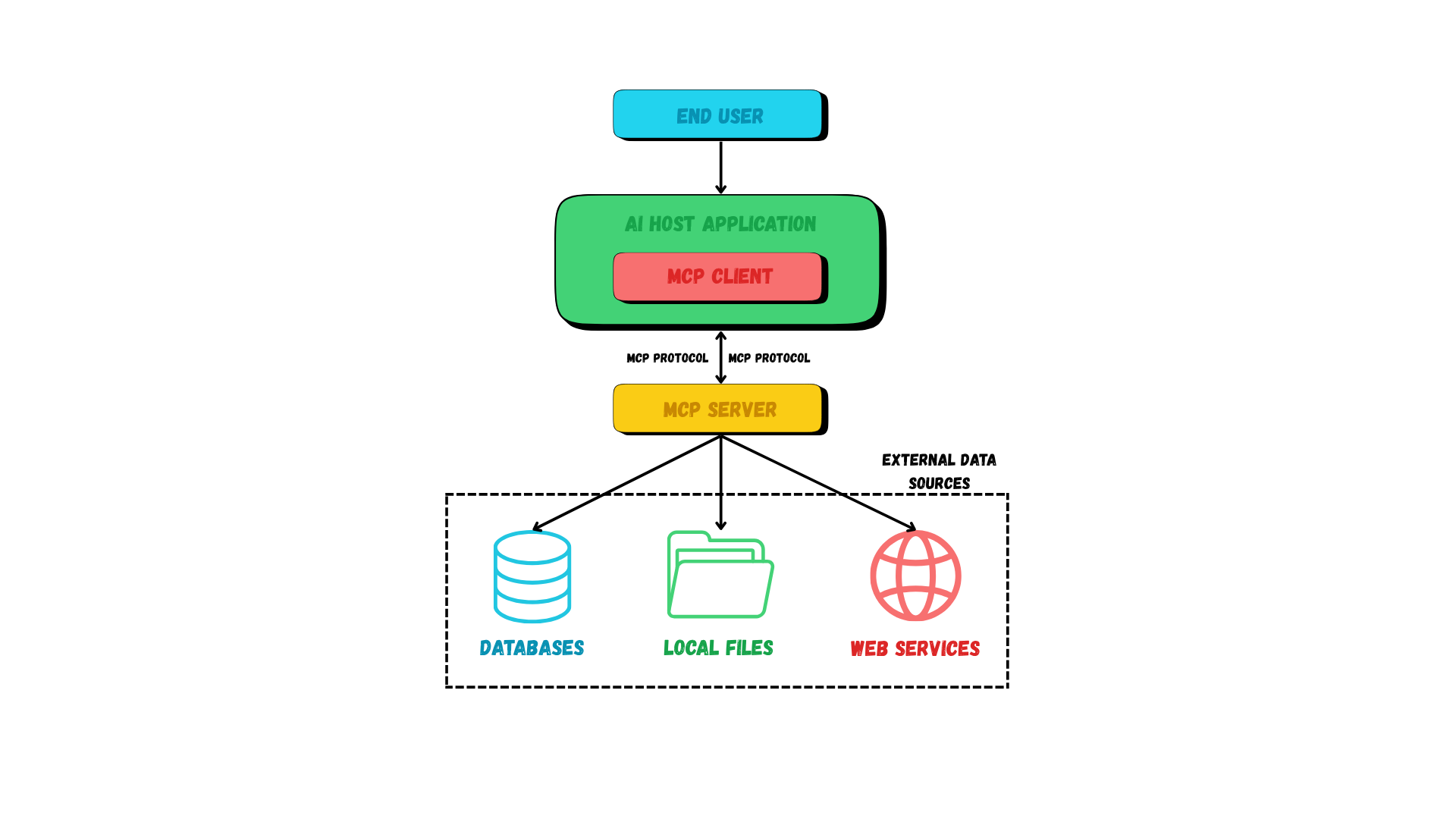
MCP is based on a client-server architecture where:
-
The host is an AI-powered application that the end-user interacts with. Examples: IDEs (like Cursor), desktop AI assistants (like Claude Desktop)
-
The AI models (Like Claude AI, Gemini, etc) act as clients. These are typically present in a host.
-
Different data sources and tools implement MCP servers.
Please check the Architecture Diagram for a better understanding:
Why MCP Matters for Pentesters and Security Professionals?
MCP changes the way we do our tedious yet exciting jobs of Pentesting by bringing all the apples (Tools 😉) in one basket where AI can work with them directly. Tools like Burp Suite, NMAP, Databases, Excel, Notion, etc. Instead of just jumping back and forth on each tool and trying to find and match data by ourselves, we can just tell AI something like “Check the latest Burp scan for SQL injection issues and compare it with the Nmap result,” and Voila!! AI will do it for us. We don’t need to switch between these tools, and also no need to search for the vulnerabilities on Google.
Congratulations!!! We saved a lot of time and energy here by not switching back and forth on tools or manually looking for connections…We can now focus on bigger tasks in life, like coming up with new attack ideas, instead of the boring, repetitive stuff. Basically, MCP gives you an AI assistant who knows all your security tools and can do the tough testing stuff for you, just by asking. It makes your work quicker and way less stressful.
Now enough of theory, let’s get our hands dirty with the fun stuff…
Configuring MCP Server, Burp Suite, and Claude AI
-
Open Burp Suite Community or Professional Edition. Make sure it is updated to the latest version.
-
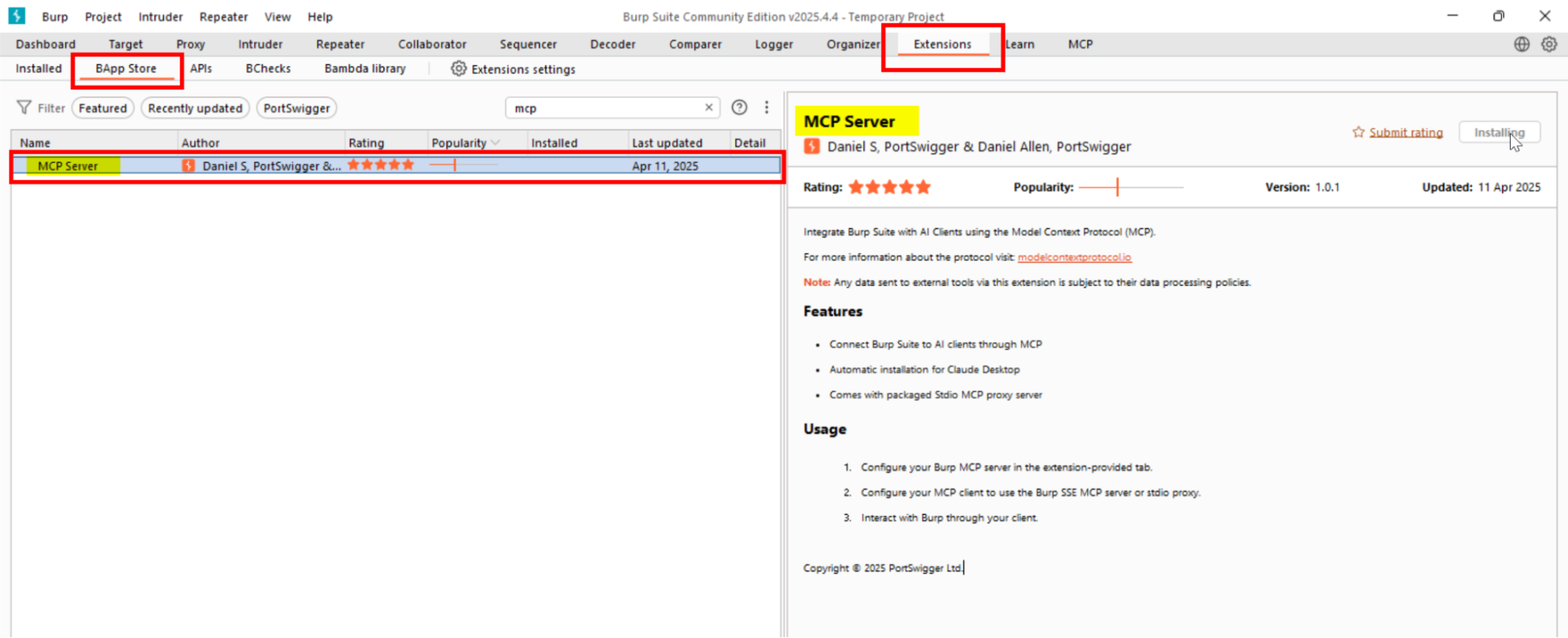
Go to the “Extensions” tab in Burp Suite and open the BApp Store.
-
In the BApp Store, search for MCP and click Install.
-
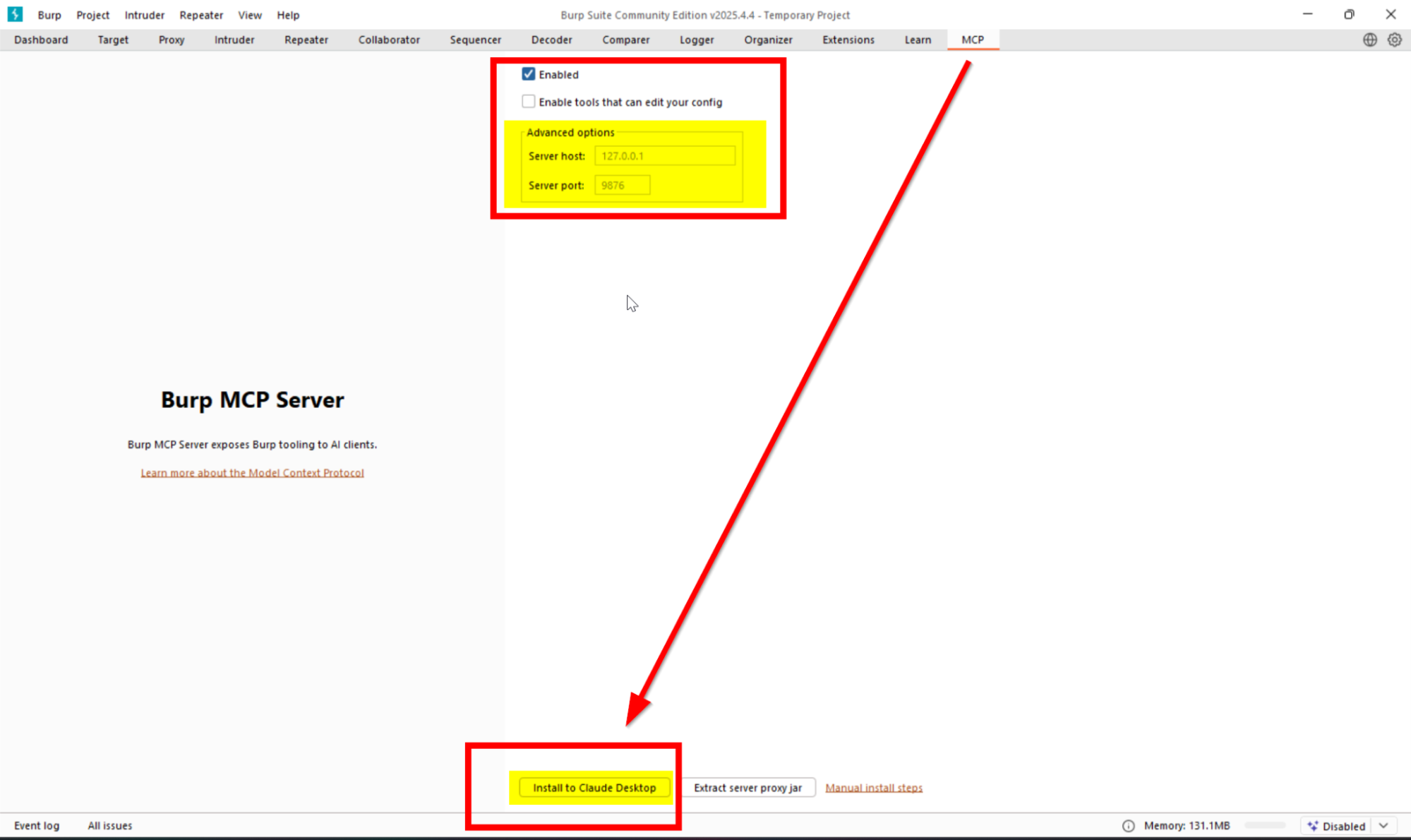
After installation, go to the “MCP” tab in Burp Suite and check if it is enabled.
-
Download the Claude AI Desktop version and install it on your system.
-
In the “MCP” tab of Burp Suite, click on “Install to Claude Desktop”.
-
Restart the Claude AI Desktop application. This step is important.
-
After restarting, you can start using Claude to send prompts to Burp Suite, and Burp Suite will respond accordingly.
In this setup, Burp Suite works as the MCP Server, and the Claude AI Desktop app acts as the MCP Client.
Next, we’re going to set up another MCP server—this time from Notion.
This will let us do two really useful things:
- Send input URLs from Notion to Burp Suite for testing
- Automatically generate technical reports in Notion based on scan results.
Steps to set up the MCP Server in Notion:
Step 1: Install the Notion App
Download and install the Notion desktop application from Notion’s official site, if you haven’t already.
Step 2: Install Node.js and npm
Claude requires npm for this setup. If it’s not installed on your system, just search online for “How to install npm on [your OS]” and follow the official guide.
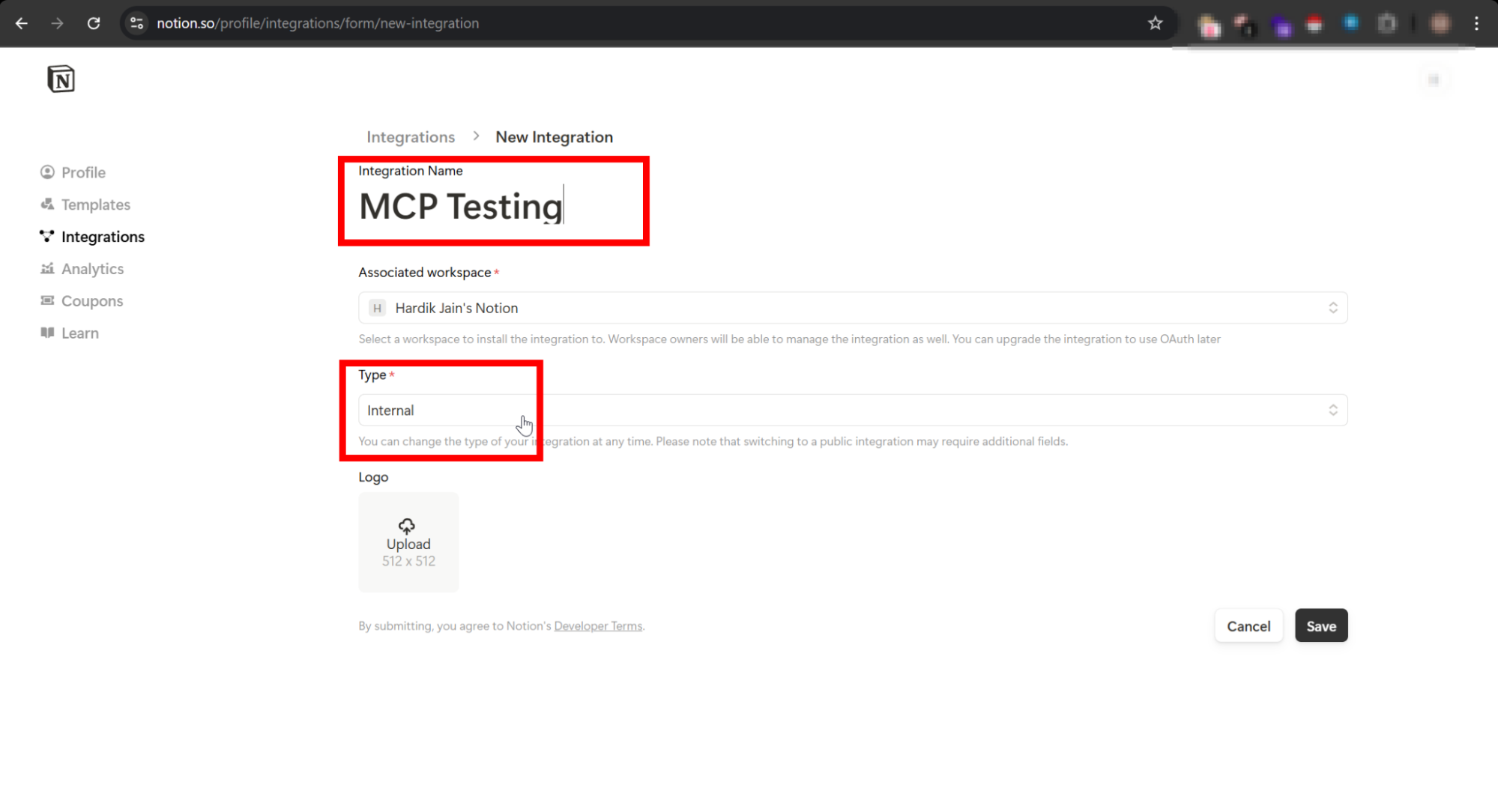
Step 3: Create a Notion Integration
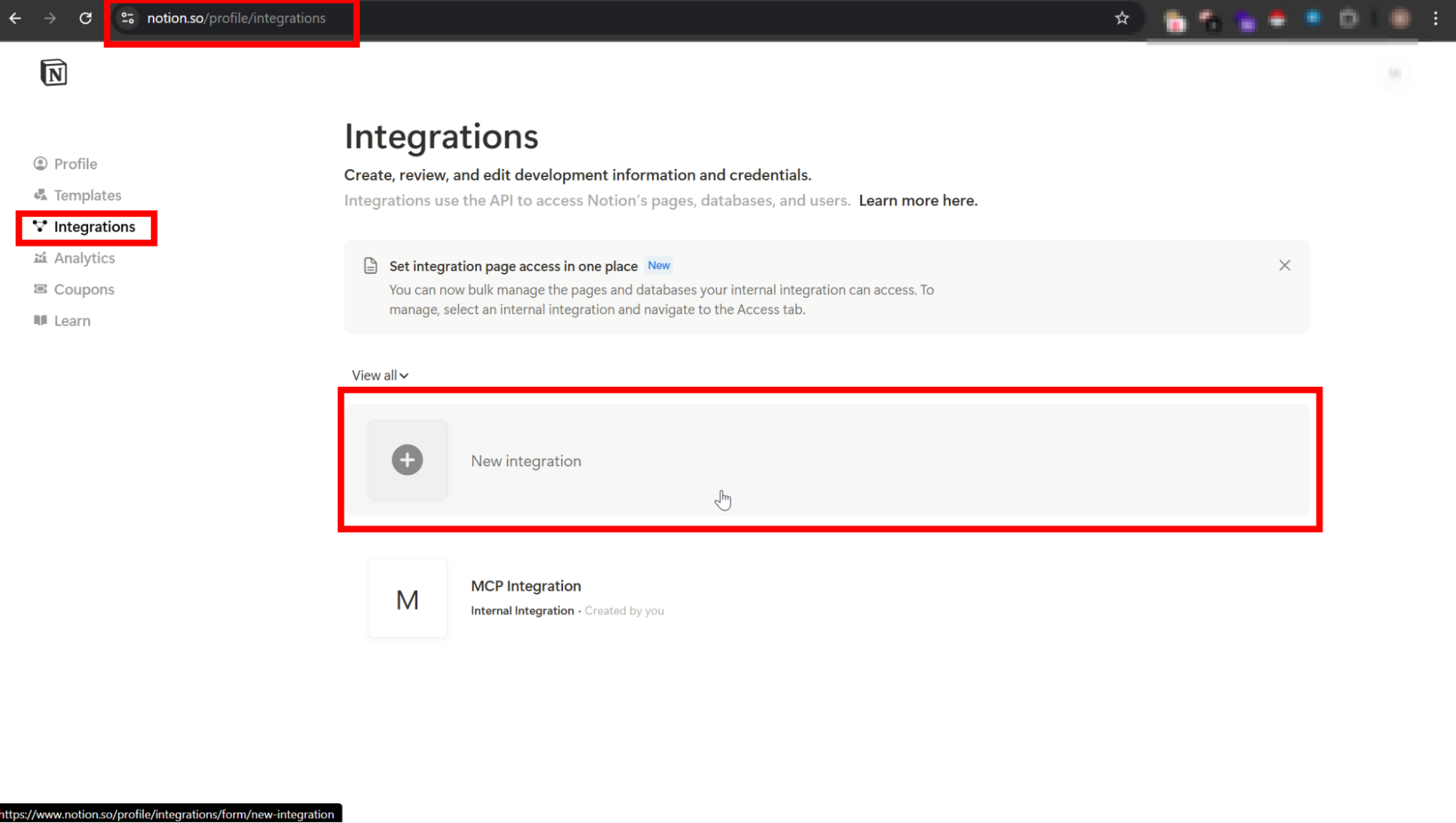
- Go to https://www.notion.so/profile/integrations.
- Click “Create new integration”.
- Give it a name and workspace access.
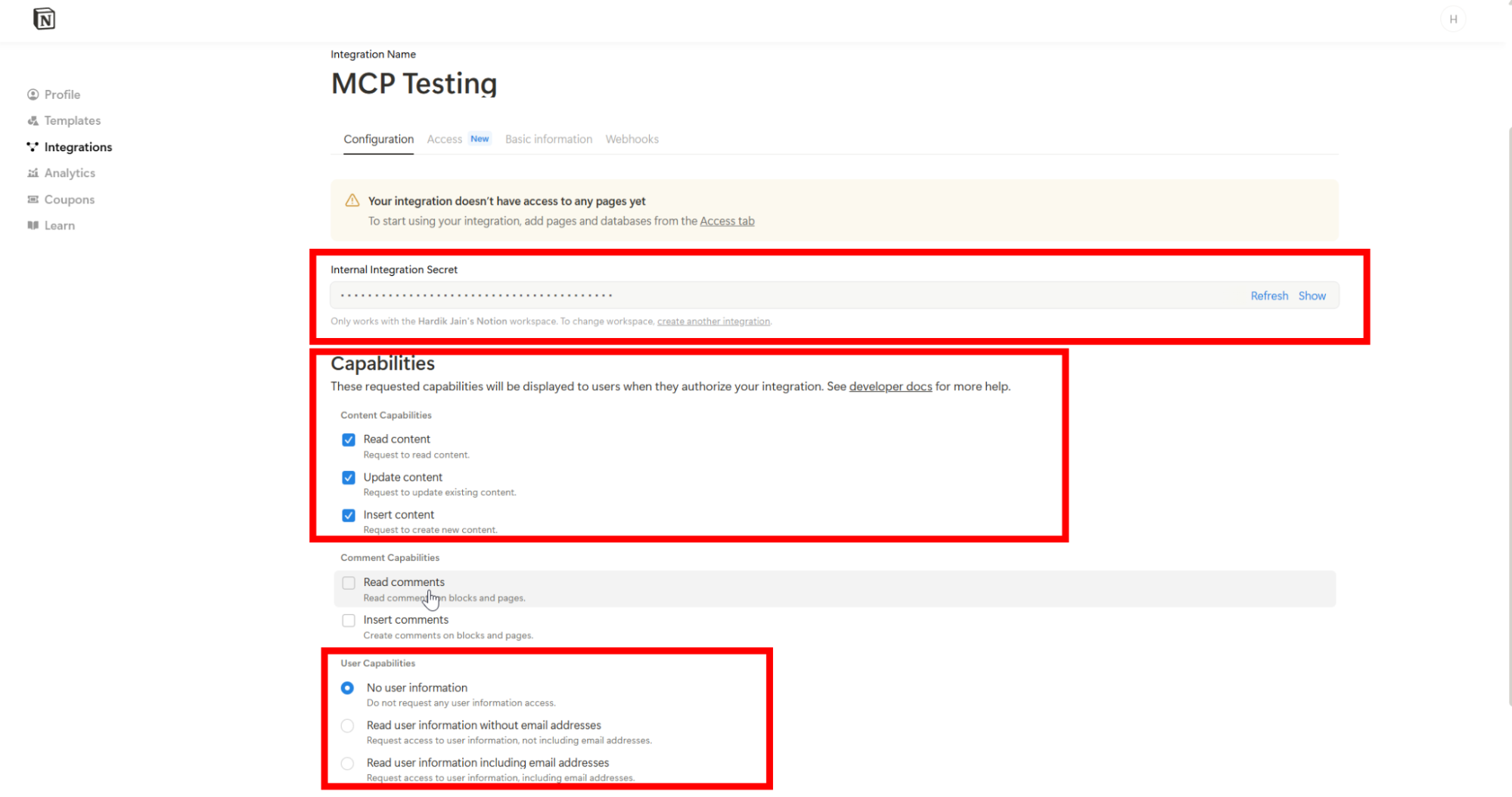
- Under Capabilities, give read and write content access.
- Copy your integration token (
ntn_...) — you’ll need it in the next step.
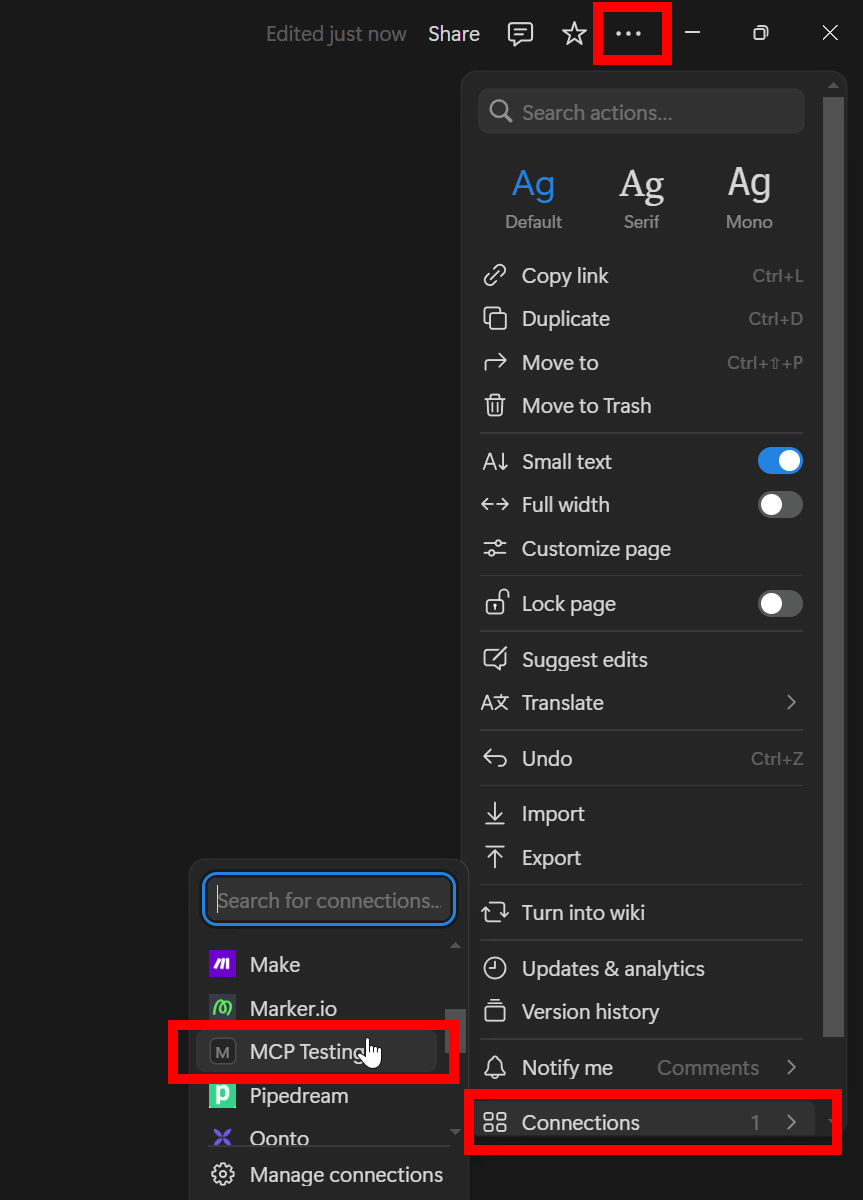
Step 4: Connect Integration to Notion Pages
- Open the Notion page or database you want to use with Claude.
- Click the three-dot menu (•••) at the top right.
- Choose “Connect to integration”, and select the integration you just created.
Step 5: Configure Claude to Talk to Notion
- Locate Claude’s config file:
On Mac:
1
~/Library/Application Support/Claude/claude_desktop_config.json
For Windows:
- Press “Windows + R”
- Search For “%APPDATA”
- Go to the Claude Folder
- Open the “claude_desktop_config.json” file
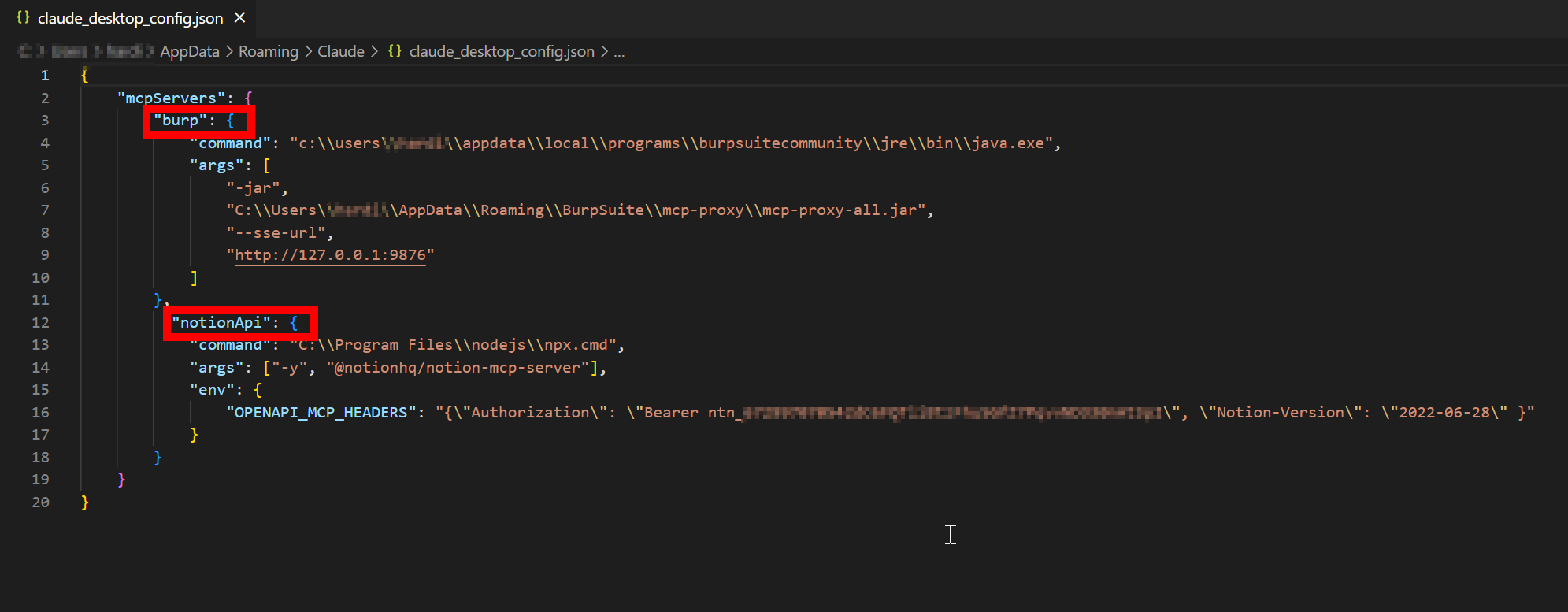
- Add the following to your
claude_desktop_config.json:
1
2
3
4
5
6
7
8
9
10
11
{
"mcpServers": {
"notionApi": {
"command": "npx",
"args": ["-y", "@notionhq/notion-mcp-server"],
"env": {
"OPENAPI_MCP_HEADERS": "{\"Authorization\": \"Bearer ntn_****\", \"Notion-Version\": \"2022-06-28\" }"
}
}
}
}
- Make sure to replace the placeholder token (
ntn_****) with your actual integration token.
Step 6: Restart Claude Desktop
Phew!!! We’re done with all the setups. Now, it’s time for Action….
Putting It All to Work
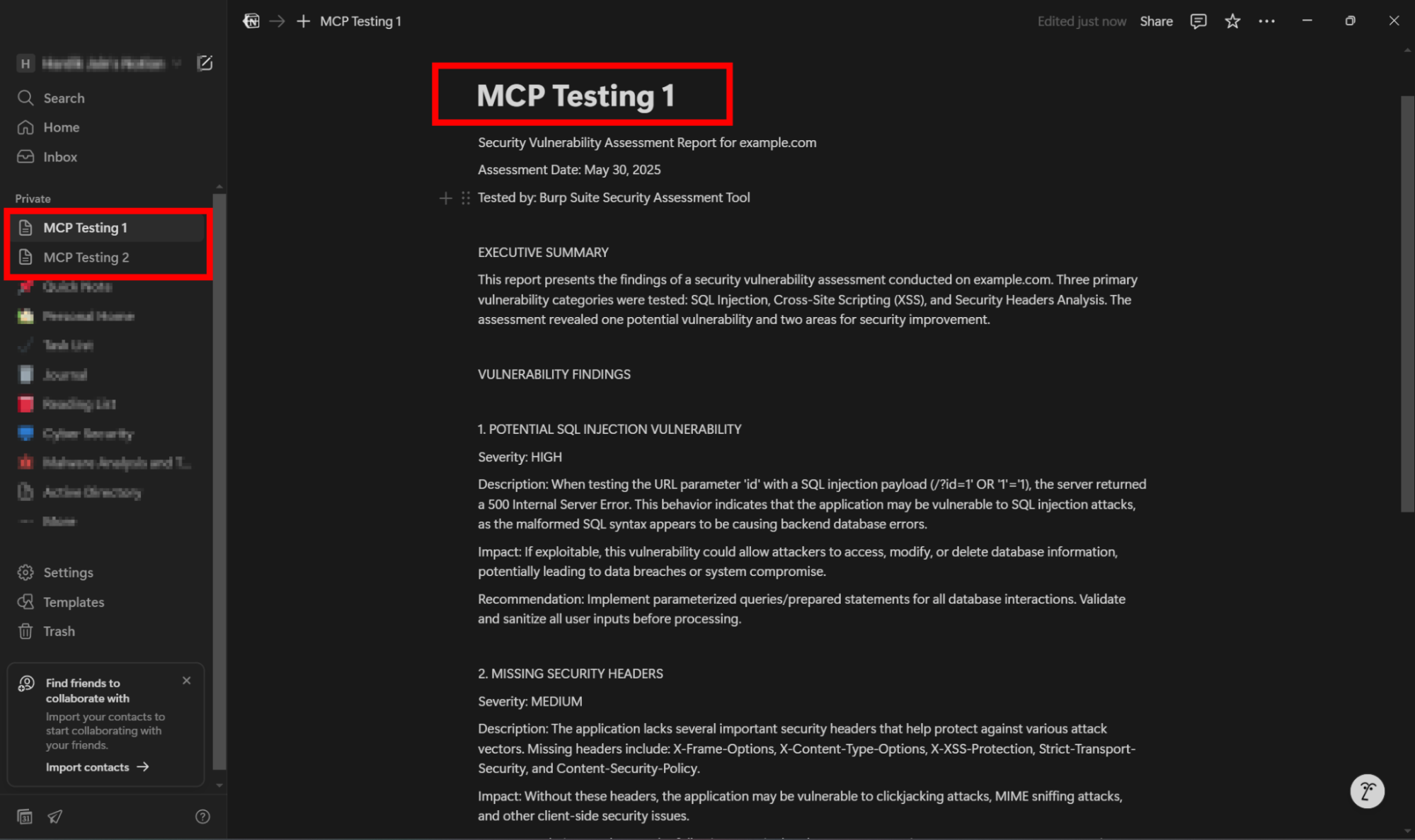
I’ve created two pages in Notion named “MCP Testing 1” and “MCP Testing 2” specifically for this demo. Both pages are connected to the MCP integration we set up earlier.
TEST 1:
Using Claude AI, I will send one domain to Burp Suite and ask it to test for three vulnerabilities. After the scan, a detailed technical report will be generated automatically on the “MCP Testing 1” page in Notion.
Prompt Used in Claude:
1
2
3
Test the website "example.com" for three vulnerabilities using Burp Suite.
Then, create a clear and well-organized report of the results and save it to
the Notion page named "MCP Testing 1."
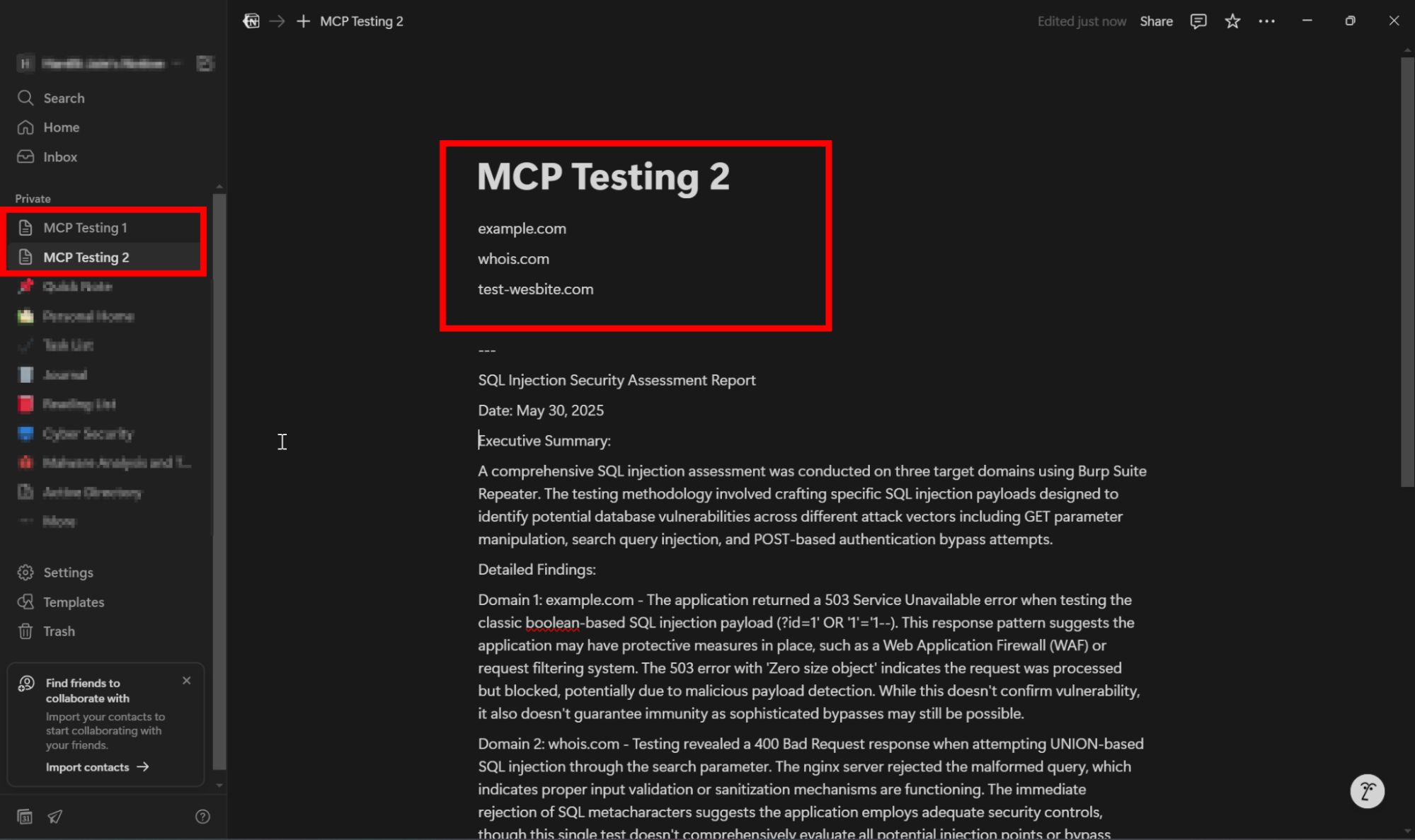
TEST 2:
For this test, I’m using the “MCP Testing 2” page in Notion, where I’ve added three domains. I’ll have Claude AI pick one domain at a time and run a quick SQL Injection test on it using Burp Suite’s Repeater tab—just one test per domain, each in its tab. After testing all three domains, Claude will put together a short, 500-word report summarizing what it found and add that right below the domains on the same Notion page.
Prompt used in Claude:
1
2
3
4
5
6
Go to the "MCP Testing 2" page in my Notion workspace. You'll find three domains
listed there. For each domain, open a new Repeater tab in Burp Suite and run a
single SQL Injection test. Test one domain at a time, using a separate Repeater
tab for each. After testing all three domains, write a concise report of about
500 words summarizing your findings and add it below the domains on the same
Notion page.
Pretty cool, right?
As you can see, everything was automated so easily. There are tons of other MCP servers you can connect with, test, and experiment with.
But hold on…
Security Concerns with MCP
We’re security professionals, and security matters most to us. While MCP makes our work way easier, we shouldn’t forget that it wasn’t designed with security as the top priority. It does have some critical vulnerabilities. Not only does MCP have its risks, but it also possesses and amplifies the vulnerabilities of LLMs
Let’s go through them briefly:
LLM-Specific Vulnerabilities:
-
Prompt Injections: A classic vulnerability where an attacker could hide any malicious instructions in user inputs or retrieved data.
-
Data Leakage: The AI can accidentally expose private or sensitive details through its responses or generated content.
-
Unauthorized Decision-Making: An attacker could manipulate AI to autonomously execute actions that are outside its permitted scope or have ill intent.
-
API Vulnerabilities: The LLM calls an external API that already has vulnerabilities.
-
Training Data Poisoning: Attackers try to insert bad data into what the AI learns from.
MCP-Specific Risks:
-
Tool Poisoning: If an attacker changes tool descriptions or outputs, the AI might get misled and use tools incorrectly.
-
Privilege Abuse: Over-permissioned tools can be misused by AI. A classic example would be an AI sends delete commands to a tool that was only meant for reading logs
-
Tool Shadowing: A malicious MCP server mimics a trusted one
-
Sensitive Data Exposure: Improper configurations may leak credentials, tokens, or private content.
But don’t you guys worry!!! We have “Jugaad” (also known as a workaround) for everything.
Let’s be super clear about one thing: MCP itself isn’t some rogue villain! One of the most dope advantages of MCP is its design for fully local deployment. This means you can run both the MCP Client and MCP Server locally on your machine, without worrying about exposing personal or confidential data to the internet.
The local setup ensures that your AI operates fully within your personal or organizational boundaries and a controlled environment.
How to achieve a Local setup?
We can use Ollama. Ollama allows us to download and run powerful AI models directly on our hardware, eliminating the need to send data to cloud-based LLMs. Ollama works as the AI Host, directly interacting with the MCP Client, i.e, Claude AI Desktop App in our case. We can also deploy lightweight MCP servers on our machines. These servers act as local, secure, custom gateways to your local resources. Examples: You can use a self-hosted GitLab or GitHub Enterprise instance to analyze code, make commits, etc. To create tickets on Jira, ServiceNow, or Remedy. To use Obsidian as your local vault for all your databases out there. To query any specific documentation in your organization’s XWiki or Confluence pages, etc.
For organizations, this isn’t just a win; it’s a strategic advantage! MCP might not have been born secure, but with local deployment, you’ve basically pulled a Tony Stark in a cave with a box of scraps. You made something secure, powerful, and totally yours.
Conclusions
It is amazing to see how far we have come as security professionals. From manually creating scripts for automation and testing each and every endpoint manually to just typing it out in natural language as if we are talking to a friend, and hours of work done within a second.
MCP has indeed opened great doors for future AI tech, where it understands and works as and when you want. But as rightly said by Uncle Ben, “With great power comes great responsibility.” We saw that MCP is insanely handy, but it isn’t security-first. Using local deployment could help you reduce your worries about security concerns, but it surely doesn’t eliminate them.
So yes. MCP — explore it, experiment with it, have fun pushing its limits…but always keep your security hat on.
Thank you.