Threat Intelligence Strategies Against Malware: How a YouTube Campaign Unraveled a Bigger Story
Presented by Pavan Karthick & Abhishek Mathew at BSides Mumbai 2024
Malware isn’t hiding in shady corners of the internet anymore, it’s front and center, often disguised within everyday platforms like YouTube. At BSides Mumbai 2024, cybersecurity researchers Pavan Karthick and Abhishek Mathew delivered a detailed session on how a simple YouTube video led them down the rabbit hole of a full-blown malware campaign. This wasn’t just a theoretical overview, it was a firsthand account of active tracking, sandbox evasion, automation, dark web research, and even blockchain misuse.
The Changing Threat Landscape
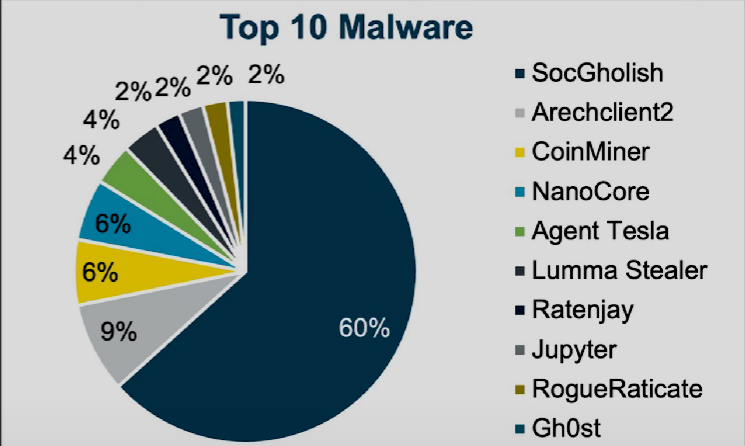
The session began with a sharp look at the recent IBM Cyber Threat Intelligence Report. One of the biggest changes seen in 2023 was the surge in InfoStealers a 266% increase, to be exact. These types of malware silently extract saved credentials, cookies, session tokens, and autofill data. Interestingly, 32% of attackers have shifted from ransomware to stealing and selling credentials, since enterprises have become more resilient to ransom demands.
Another key stat: Valid Account Usage for initial access is rising fast. While phishing is still common, attackers now rely on previously compromised credentials to log in directly. And where do these credentials come from? Malware.
“InfoStealers are now the front door to enterprise breaches.”
Additionally, Malvertising or Malicious advertising has emerged as a leading malware distribution method. Attackers poison search results with fake download sites. In Q1 2024 alone, 79% of malware infections stemmed from ad-based delivery.
SoapGalish & Brute Force via Browsers
One specific malware family the speakers detailed was SoapGalish. It’s a JavaScript-based stealer that infects browsers and uses them to brute force WordPress login pages. Unlike traditional botnets, this malware utilizes the network of each infected user to initiate distributed brute force attempts. This evades rate limiting and avoids detection because each request appears to come from a different IP that is the victim’s browser.
It also abuses a known WordPress vulnerability : User Enumeration, to discover valid usernames before launching password guessing attacks. Once a site is compromised, it’s used to spread further, creating a chain infection.
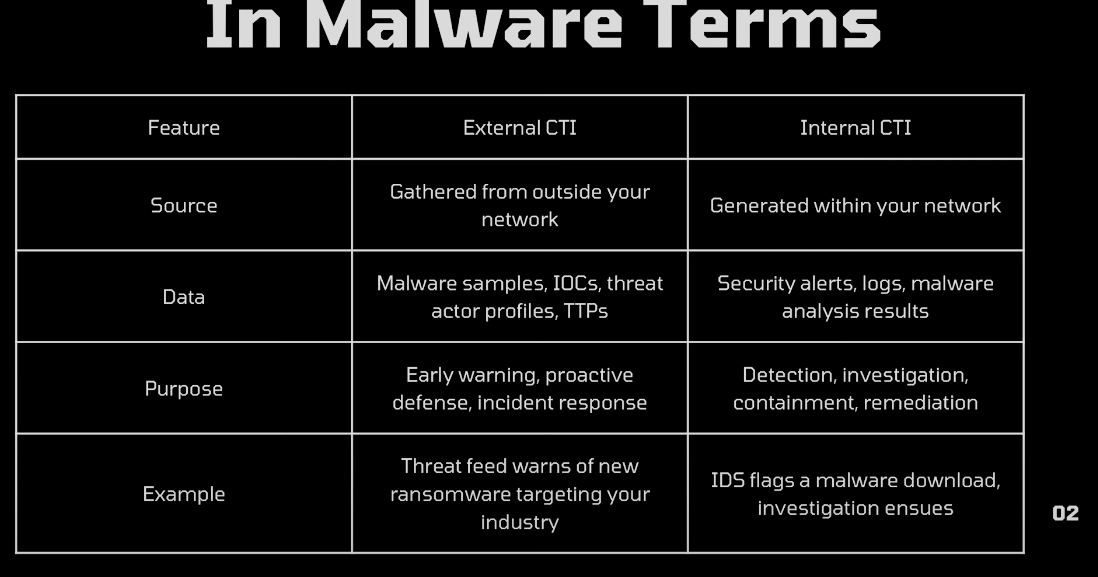
Internal vs External CTI
The researchers walked through the key differences between Internal Cyber Threat Intelligence (CTI) and External CTI:
- Internal CTI involves insights from your own logs, SIEMs, XDR, and insider threat monitoring. It detects anomalies like unusual login times or access to restricted files.
- External CTI provides context from the wider threat landscape: malware trends, active APT groups, dark web chatter, and shared IOCs.
They shared examples like the Clop ransomware group’s exploitation of the MOVEit vulnerability. External CTI identified the threat early, but many orgs failed to act in time.
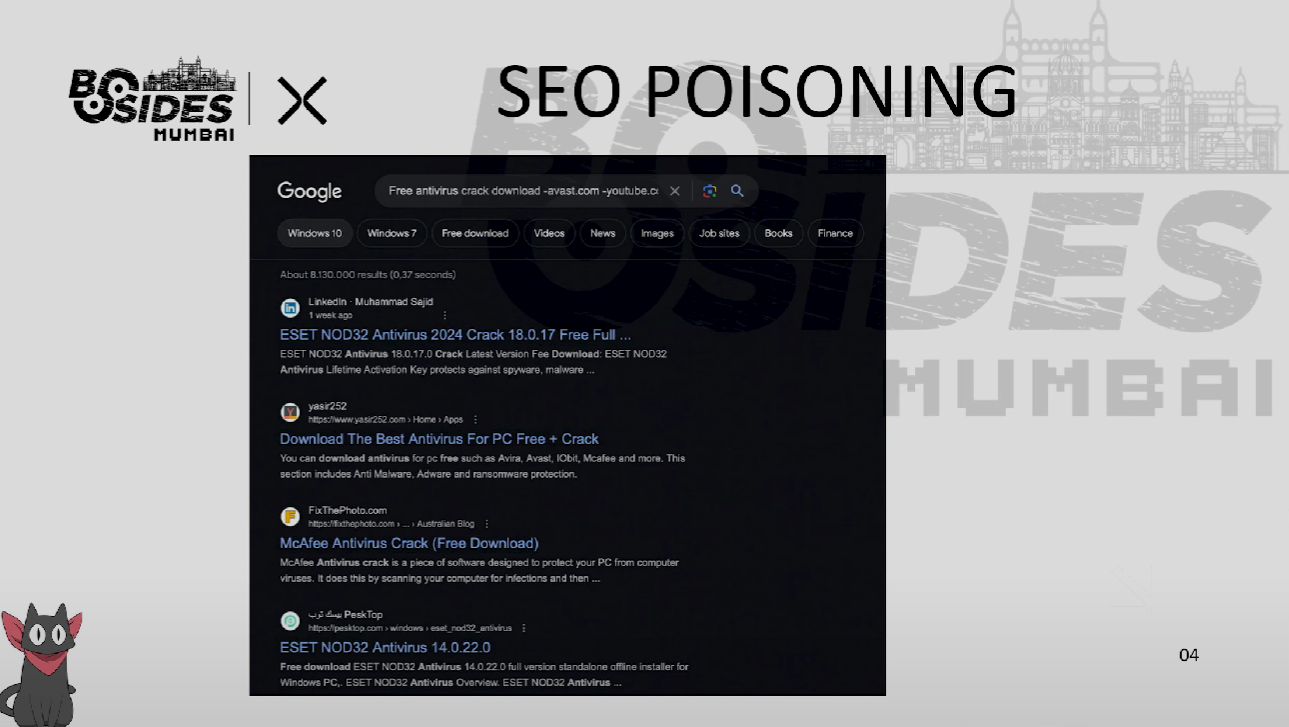
YouTube as a Malware Platform: SEO Poisoning in Action
The central case study was both fascinating and disturbing. Attackers had compromised legitimate YouTube channels and uploaded AI-generated tutorial videos promoting cracked software like Adobe, Premiere Pro, or antivirus tools. These videos often ranked highly due to keyword stuffing and SEO optimization.
The attack flow:
- Victims clicked on links in the video descriptions.
- They were redirected through multiple cloaking domains.
- The final payload was often hosted on Mediafire, Dropbox, or Google Drive.
- Payloads came in encrypted ZIP files to bypass antivirus detection.
- These ZIPs expanded from 10MB to 800MB+ executables filled with junk to evade sandbox size limits.
Over just two months:
- 250,000+ videos were uploaded
- 800 malware samples captured
- 10+ malware families observed
- 1 Crore+ views estimated
Only 10% of these samples were detected by public sandboxes, meaning 90% flew under the radar.
Sandbox Evasion in the Wild
When the malware was detonated in test environments, it appeared harmless. But that was the point.
It had built-in sandbox evasion tactics:
- Checking for VM environments
- Looking for analysis tools (Wireshark, Procmon, etc.)
- Detecting user inactivity (no mouse movement)
- Verifying hardware configurations
If any red flags were found, it stayed dormant.
Automating the Hunt: YouTube Malware Tracker
To keep up with the campaign’s scale, the team built a complete automation pipeline:
- YouTube Scraper — Fetched metadata and video descriptions
- Keyword Matcher — Identified videos using tags like “crack”, “license key”, “download”
- Redirect Crawler — Followed URL hops to find final payload
- Malware Sample Hunter — Downloaded ZIPs and unpacked them
- Custom Sandbox — Ran files in stealthy VMs
- Behavioral Logger — Captured network calls, file activity, dropped files
They even tracked how the number of malicious uploads changed daily, analyzing 500–600 new videos every single day.
Using AI to Deobfuscate Malware
The team used Claude AI and ChatGPT to accelerate malware analysis. These LLMs helped them to:
- Decode base64 and hex blobs
- Deobfuscate JavaScript loaders
- Interpret logic inside packed files
- Generate basic scripts for automation
Instead of manually tracing function calls, they were able to reverse engineer complex JS loaders in minutes.
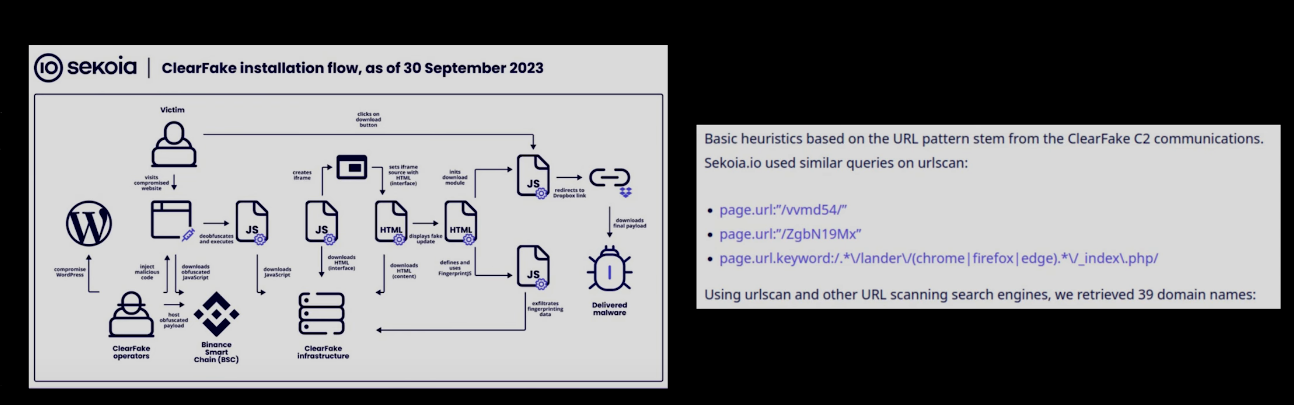
Blockchain-Powered Malware: The ClearFake Case
Perhaps the most novel discovery was how malware authors used Ethereum smart contracts to store and distribute JavaScript payloads.
Here’s how it worked:
- A compromised site loads a smart contract.
- The smart contract contains a 41-byte hash acting as a key.
- This triggers the loading of malicious JavaScript.
- Attackers avoid C2 takedowns since smart contracts live permanently on-chain.
By tracing these transactions and decoding JS, the team identified:
- 579+ infected domains
- 95+ obfuscated JavaScript files
- 4+ malicious active smart contracts used for malware delivery
Following the Cookie Trail
In another case, they reverse-analyzed browser cookies exfiltrated by malware. These cookies revealed the infected user’s navigation history:
google.com → okrush.com → currentpc.com → scloud.ws
By identifying “breadcrumb” domains, they mapped out infection paths and infrastructure clusters. This helped them build indicators beyond just hashes and domains.
Tools That Helped
The team highlighted tools like:
- BeautifulSoup for HTML parsing
- N8N for automation without much coding
- URLScan for passive DNS and screenshotting
- Custom Python scripts to extract transaction hashes and JavaScript payloads from blockchain
They emphasized how tools + creativity go hand-in-hand in real threat hunting.
“We’re not script kiddies anymore. We’re ChatGPT kiddies.”
Final Thoughts: Modern CTI Needs a Mindset Shift
This talk wasn’t about just collecting indicators. It was about building intuition.
Threat intelligence today is about:
- Recognizing infrastructure patterns
- Using AI and automation as force multipliers
- Investigating creatively, beyond traditional telemetry
If you’re still relying only on feeds and SIEM alerts, you’re reacting to yesterday’s attacks. Pavan and Abhishek showed that real CTI is proactive, investigative, and deeply technical with a human at the core of it all.
Stay curious. Stay creative. And stay hunting.